Active Directory auditing is an important part of ensuring compliance and the security of the IT environment. However, a common problem that Active Directory auditors face is how to identify the source of account lockouts. If a user account gets locked out for any reason, such as password modifications, may result in downtime and it can often be a time consuming and frustrating process to get the AD account re-enabled.
Follow the below steps to track locked out accounts and find the source of Active Directory account lockouts. If you already know the lockout account in question, you can start directly from step 5 (to track source).
Step 1 – Search for the DC having the PDC Emulator Role
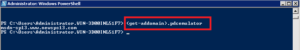
The DC (Domain Controller) with the PDC emulator role will capture every account lockout event with an event ID 4740. In case you have only one DC then you can skip this step.
Get-AdDomain – Running this cmdlet will search for the domain controller having the role of a PDC emulator.
Step 2 – Look for the Event ID 4740
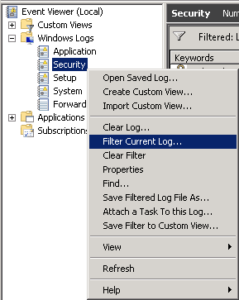
Open the event log viewer of the DC. Go to the security logs, and search for the Event ID 4740.
Step 3 – Put Appropriate Filters in Place
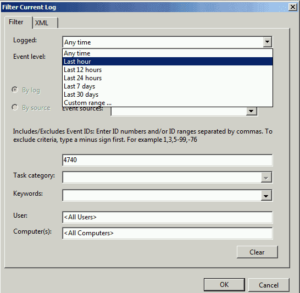
There are suitable filters to generate a more customized report. For example, you can search for a lockout which occurred in the last hour, and find the recent lockout source of a particular user.
Step 4 – Find Out the Locked Out Account Event Whose Information is Require
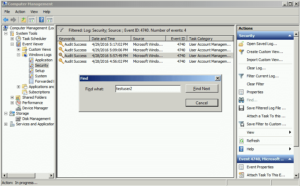
Click on the “Find” button in the actions pane to look for the User whose account has been locked out.
Step 5 – Open the Event Report, to Find the Source of the Locked account
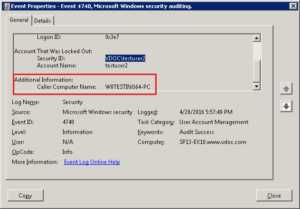
Here you can find the name of the user account in the “Account Name”, and the source of the lockout location as well in the ‘Caller Computer Name’ field.